Click the Schema Inspector icon in the JADE program folder, to run the standalone Schema Inspector application.
The Schema Inspector sign-on form is then displayed. The user id of your workstation is displayed in the User Id text box, by default.
As your password is hidden for security reasons, each character is represented by an asterisk (*) character.
The user id and password are case-sensitive.
Specify your user id and optionally your password in the appropriate text boxes, and then click the OK button to sign on to the Schema Inspector.
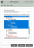
The Schema Inspector dialog, shown in the following image, is then displayed.
In the Select Schema to inspect combo box, select the schema whose instances you want to inspect. The classes list box is then populated with all classes in the selected schema.
In this list box, select the classes whose instances you want to inspect.
As the classes list box is a multiple-selection list box, you can use the Shift or Ctrl key to select a group or range of classes.
When you have selected the required classes, click the OK button. If security is not set, the Schema Inspector is then displayed. Alternatively, click the Cancel button to abandon your selections.
If security is set for a selected class and you do not have sufficient security, a message box is displayed, informing you that you do not have sufficient security to inspect instances of the specified class.
Perform one of the following actions.
-
Select another class to which you may have inspection access rights.
-
Select the Logoff command from the File menu to display the Schema Inspector sign-on form and specify a user id and password that permit access to the classes whose instances you want to inspect.
-
Select the Exit command from the File menu, to close the Schema Inspector.