Locating Possible Transient Object Leaks
The Schema menu in the Schema Browser enables you to scan all methods in a schema or class for possible transient leaks.
The transient leak analysis can report potential leaks that are not in fact leaks, for reasons that are outside of the understanding of the analysis. You can mark such entries for exclusion from the report that is produced, by placing the following tag (which must be enclosed within [ ] bracket symbols) in a comment on the same line as the method call.
[ExcludeFromTransientLeakReport]
The following code fragment examples mark lines of code for exclusion from the transient leak analysis.
create cust transient; // create the customer [ExcludeFromTransientLeakReport]
cust := methodReturnsTransient(); // [ExcludeFromTransientLeakReport]
Note that for multiple‑line function calls, the // [ExcludeFromTransientLeakReport] comment must be placed on the same line as the method call, instead of that of the method parameters. For example, the first of the following code fragment comments does not exclude the potential leak, but the second example does.
var := methodReturnsTransient(parameter1,
parameter2); // [ExcludeFromTransientLeakReport]var := methodReturnsTransient(parameter1, // [ExcludeFromTransientLeakReport]
parameter2);
In addition, JADE provides a PossibleTransientLeaks global constant category that contains the "ExcludeFromTransientLeakReport" global constant.
To locate possible transient object leaks in the schema selected in the Schema Browser
-
Select the Find Possible Transient Leaks command from the Schema menu.
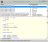
The Find Possible Transient Create Leaks dialog, shown in the following image, is then displayed.
The name of the schema selected in the Schema Browser is displayed in the first combo box in the Search Criteria group box.
-
If you do not want to search for possible transient leaks involving local variables and parameters in all methods in the schema selected in the Schema Browser (the default value), perform one of the following actions in the Search Criteria group box.
-
Select another schema in the combo box below the Search selected schema for all creates option button if you want to locate possible transient object leaks in a schema other than the one currently selected in the Schema Browser.
-
Select the Search all schemas option button if you want to locate possible transient leaks in all methods in all schemas.
-
Select the Search selected schema and all sub-schemas option button and in the combo box above the option button, select the schema in which you want to locate possible transient leaks in all methods in that schema and its subschemas.
-
Select the Search for creates of selected class in all schemas option button and in the Select the schema above to get its list of classes combo box below the option button, select the class of the schema selected in the combo box beneath the Search selected schema and all sub-schemas option button that has a local copy class whose methods will be scanned for possible transient leaks.
All creates of that class in all schemas are searched; that is, the search is performed in the schema in which the class is defined and all subschemas. If the class is a RootSchema class, all schemas are searched.
For details about filtering the entries displayed in the list box associated with the combo box, see "Filtering Entries in Combo Box and List Box Text", in Chapter 2.
-
-
Uncheck the Report created objects not deleted check box if you do not want to locate any transient create statement leaks on local variables or method parameters where there is no delete of that variable and that variable was not returned by the method and was not passed as a parameter to another method.
By default, this check box is checked, indicating that created objects are checked for deletion.
-
Uncheck the Report created in loop but not deleted in loop check box if you do not want to locate possible leaks where a create is performed inside a loop but the delete is outside of the loop. This may not actually be a leak, because only one create may have been performed.
By default, this check box is checked, indicating that objects created in a loop are checked for deletion within that loop.
-
Check the Report objects not deleted but assigned check box if you want to locate creates performed where there is no delete, but the variable was assigned to another property or variable. This may not represent a leak, as it is not known whether this value is subsequently deleted.
By default, this check box is unchecked, indicating that assigned objects are not checked for deletion.
-
Check the Report objects not deleted but passed to other methods check box if you want to locate creates performed where there is no delete, but the variable was passed as a parameter to another method. This may not represent a leak, as it is not known what subsequently happens to that object.
By default, this check box is unchecked, indicating that objects passed to other methods are not checked for deletion.
-
Check the Report created objects returned from method check box if you want to locate creates performed where the object is returned from the method. This may not represent a leak, as it is not known what the calling method will do with that object.
By default, this check box is unchecked, indicating that objects returned from methods are not scanned for possible leaks.
-
Check the Report deletion not performed in epilog check box if you want to locate objects that have been created and deleted but where the object is not deleted in the epilog section of the method. This situation would result in a leak if an exception occurred during the method call.
By default, this check box is unchecked, indicating that epilogs are not scanned for possible leaks.
-
Check the Ignore [ExcludeFromTransientLeakReport] tags check box if you want method lines containing this tag in a comment to be analyzed for possible transient leaks instead of being ignored.
By default, this check box is unchecked, indicating that method lines that contain the [ExcludeFromTransientLeakReport] tag are ignored during the possible transient leak analysis.
-
In the Output Options group box, select the Print Preview option button if you want to preview the possible transient leaks report output.
By default, the Methods List Browser option button is selected, indicating that the methods in which there are possible transient leaks are displayed in a Methods Browser, shown in the following image, so that you can edit the method source whose transient leak list entry you have selected.
-
Click the Search button to initiate the search. Alternatively, click the Cancel button to abandon your selections.
The following image is an example of the possible transient leaks displayed in a Methods Browser.
When you press Tab to move focus from the table of methods at the top of the browser to the editor pane, the cursor is positioned at the left of the source line in which the possible transient leak has been identified.
From JADE version 2020, the possible transient leaks listed in the upper pane of the Methods Browser are now sorted in ascending order of the Method column (that is, by schema, class, and method). Left‑click on the first row (the column header) of the table to sort the possible transient leaks in descending order (that is, Z through A or 9 through 1) using the contents of the clicked column. Click the same column again to toggle the order of the entries. The column that is used for sorting displays an arrow icon to indicate whether the sorting is in ascending (˄) or descending (˅) order.
The result of your search is output to a report that is displayed in a Methods Browser or in print preview mode, depending on the option that you selected in step 10 of the previous instruction. This report contains the:
-
Schema of the method
-
Class in which the method is defined
-
Method name where the create was performed
-
Line number of the create statement in the method
-
Type of the object being created
-
Variable name used in the create statement
-
Description of the possible leak
The report will also track calls to RootSchema methods that create and return a transient object that needs to be deleted (for example, Class::allProperties) and methods scanned that return a transient object that was created. If a possible leak is detected for such situations, the description will include the method name involved and the line number will be the statement in which the call was made.